- Solutions
- ShieldVision™
- By Use Case
- Industries
- Compare Us
- SOC
- Visibility Triad
- Knowledge Center
- Partners
- Company
- Talk to an Expert
The MITRE ATT&CK Framework is a knowledge base of tactics and techniques that can be used as a foundation for classifying adversary behaviors and assessing an organization’s vulnerabilities.
Created in 2013 by the MITRE Corporation, a non-profit supporting U.S. government agencies, it is one of the most comprehensive sources for classifying threats and developing models.
The ATT&CK portion of the name stands for Adversarial Tactics, Techniques, and Common Knowledge.
Simply put, you can imagine the MITRE ATT&CK knowledge base a “Wikipedia” of cyber threats and tactics.
MITRE is a government-funded research organization. The company was born out of MIT in 1958. MITRE started ATT&CK in 2013 to document common tactics, techniques, and procedures (TTPs) that advanced persistent threats use against Windows enterprise networks. It was created out of a need to document adversary behaviors for use within a MITRE research project.
The MITRE ATT&CK Matrices are tactics and techniques laid out in a “periodic table” of tactics and techniques used by threat hunters, defenders, and other cybersecurity professionals to classify attacks and assess an organization’s risk.
The most popular framework used is the MITRE ATT&CK® Matrix for Enterprise.
The matrix contains information for the following platforms: Windows, macOS, Linux, PRE, AWS, GCP, Azure, Azure AD, Office 365, SaaS, Network.
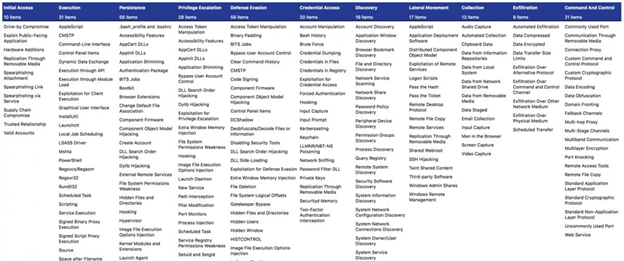
The MITRE ATT&CK Tactics represent the “why” of a technique. What is the adversary’s objective when performing an action? Tactics give important context to the offensive action.
Techniques are the “how” component of the action, how an adversary achieves the tactic. They may also represent the “what” an adversary gains by performing an action.
There are a number of ways an organization can utilize the MITRE ATT&CK framework, here are just a few:
When choosing a Managed Security Service Provider (MSSP) for outsourced threat detection and response services, the MITRE ATT&CK Framework proves its value in a Security Operations Center (SOC).
Lumifi uses the MITRE ATT&CK framework in several ways.
First, our content team maps each of our alerts to a technique, which allows us to see where our detections are heaviest and where we need to expand our ruleset.
When our analysts are threat hunting, they use MITRE techniques as guides for Tools, Techniques, and Procedures (TTPs) that they should be on the lookout for. Doing so allows us to find gaps in customer visibility.
One use case is if a customer gets all their alerts in the Reconnaissance phase, but not much else, we can assume they are not receiving all relevant data. This would start a process where we take another look at their environment and see if their critical logging source has changed their logging format.
Another added benefit is trend data. Lumifi receives alerts across our clients’ environments collectively, where they can be categorized using the MITRE framework. For example, if there is a spike in Initial Access through phishing, like the initial onset of COVID-19, or an influx in Supply Chain attacks in the SolarWinds fiasco.
Our customers receive more information so they can become more granular with their defense strategies and focus on weak areas. For example, if we see a customer with a large amount of phishing emails, they may need to step up their email filtering. Or if we see an increase in privilege escalation, defense evasion, or credential access, we should figure out the origin of these attacks and ensure the customer has a solid Endpoint Detection and Response platform.
MITRE allows Lumifi to identify gaps in security and give a broad picture of where our SOC should focus and how to better assist our clients.
Every level of our security operations team uses the MITRE ATT&CK framework, from reporting to tasking the threat content team to see if customers need specialized assistance or guidance.
Lumifi's proprietary orchestration tool, SHIELDVision, utilizes the MITRE ATT&CK framework in order to provide concise identification and feedback.
We utilize the framework in our automated scans, hunting scans, and investigations. Analysts make sure to list the Access and Technique according to the framework.
Customers can rest easier knowing we are mapping their networks to the MITRE framework and receive additional insight in their quarterly calls with our engagement team.
The MITRE ATT&CK Framework is an important tool for red and blue teams alike. Whether it’s emulating an attack or using the framework to inform security decisions, the MITRE ATT&CK framework is a useful piece of the cybersecurity landscape.
Leading MSSPs utilize the framework in order to provide in-depth investigations, threat hunt, and create clear communication with their customers.
To learn more about how Lumifi uses the MITRE ATT&CK Framework and how we can protect your network, contact us today.

Subscribe to Lumifi's Daily Cybersecurity News Curated by a CISO
Date: 02.28 | Time: 10:00 AM MT