- Solutions
- ShieldVision™
- By Use Case
- Industries
- SOC
- Visibility Triad
- Knowledge Center
- Partners
- Company
- Talk to an Expert
Learn about the difference between SCADA and IoT systems and how they work and compare to one another.
Supervisory control and data acquisition (SCADA) systems have been used for decades to monitor and control production facilities or equipment across industries such as oil and gas refining, energy distribution, water management, waste control and telecommunications.
SCADA systems are in use as a major tool for controlling industrial equipment since the 1960s.
A SCADA system works by collecting data from local and remote sensors and sending data to a centralized command-and-control location from where central computers control remote machinery or plants.
Internet of Things (IoT) systems have emerged recently. IoT systems offer a level of automation within a machine-to-machine communication framework in which machine learning and artificial intelligence usually play a role.
IoT systems include interrelated devices that have unique identifiers (UIDs) and transfers data over a network without interaction.
While SCADA systems are standard with industrial systems, IoT adds features and functionality where SCADA ends.
SCADA and IIoT (Industrial Internet of Things) concepts and their overall system architecture face cybersecurity challenges since they are a likely target for advanced hacking groups. Control systems for industrial use are also a desired prey for government-backed hackers, which poses real challenges to the security of SCADA and IoT industrial control systems.
SCADA systems usually manage Industrial Control Systems (ICS), which in turn manage machines and other industrial equipment used in industries as varied as oil and natural gas, energy and water utilities, chemical and pharmaceutical, food and beverages, car and aircraft making and durable goods manufacturing. The same is true for industrial IoT networks, which are rapidly expanding across multiple industry verticals.
These are mostly critical industries that operate complex industrial equipment networks, often across continents. If your organization operates a SCADA or an IoT control system, you should be prepared for cyber-attacks coming from three directions:
An industrial control system will never be free of threats as it appeals to many bad actors. The number of identified SCADA vulnerabilities averages between 47 and 467 a year, according to a report by Trend Micro.
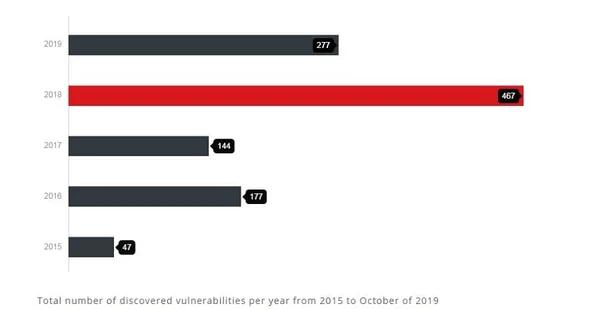
Source: Trend Micro
The number of IoT vulnerabilities is even larger when factoring in IoT systems’ untested architectures and the lack of widely adopted standardization, which in turns results in endpoint devices that are vulnerable to various cyber threats.
The existence of zero-day vulnerabilities - which are yet undiscovered vulnerabilities for anyone to exploit - is a pressing issue. Even if an organization operates in a perfect competitive environment, in which corporate espionage does not exist, critical industries and their control systems will always be a target for government-backed attacks and hackers looking for profiteering.
The claim that SCADA systems, and industrial IoT systems to a lesser extent, are not public networks and are thus harder to attack is not valid. Successful cyberattacks on oil drilling operations and nuclear power generation facilities are documented in the Middle East. Additionally, penetrations into energy distribution networks are documented in Europe (in Ukraine), in which case the attackers managed to switch off a few towns and regions off the grid.
These attacks involve both online methods and spear-phishing techniques as well as spread of Trojan malware through portable devices such as infected USB sticks.
Industry reports show about 40% of all industrial sites have at least one direct connection to a public network such as the Internet. This means that almost half of industrial sites offer the means for an attacker to test their cyber defenses and possibly penetrate their systems.
Bear in mind that many SCADA systems are still using out-of-support operating systems such as Windows XP and many IIoT systems rely on outdated firmware or insecure third-party components.
With the majority of industrial sites having at least one remotely accessible device, other attack vectors include exploiting vulnerabilities such as:
A few years ago, Kaspersky Lab reported that WannaCry malware was used to penetrate the ICS systems of manufacturing companies, oil refining facilities, smart-city infrastructure and electricity distribution networks.
The attack demonstrates how bad actors penetrate a SCADA or an IIoT system that runs within a well-protected industrial network, but where organizations have servers and workstations that are connected to several subnets inside the organization.
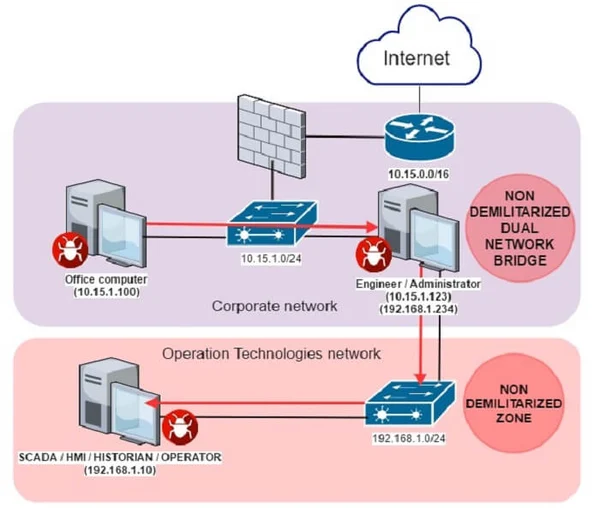
Source: Kaspersky Lab
In an ideal world, no devices within a SCADA or an IIoT network will have a direct connection to the Internet, but the chance is good for at least one device to connect to at least two subnets inside an organization’s perimeter, which in turn enables an intruder to reach their ICS from the outside.
Never underestimate the risk of someone attaching an infected device to one of your systems inside the shielded perimeter. Under this scenario, an organization may have no connection to the outside world and no data will leak outside the network, but still may see their data and systems encrypted by ransomware.
The U.S. President’s Critical Infrastructure Protection Board provides guidelines for improving the cyber security of SCADA systems, which highlights the importance of securing industrial control systems.
Recommended actions include disconnecting unnecessary connections to a SCADA network but you should be aware that - while such an isolation is theoretically possible in a SCADA architecture – IoT control systems might include connections to smart homes and smart offices, which are communicating over the Internet. In fact, IoT networks are operating exactly this way if they are not closed IIoT networks, which can be penetrated through a targeted cyber-attack.
A working cyber-security strategy to protect your SCADA, IIoT or IoT networks should involve the following measures:
Another factor to consider is regulatory compliance, as IoT implementations may involve processing sensitive personal data that is protected under the Health Insurance Portability and Accountability Act (HIPAA), the Payment Card Industry Data Security Standard (PCI DSS) or any other law that concerns data privacy and security. The same applies to SCADA systems if an organization collects personally identifiable data from consumer metering devices, for instance.
Securing a SCADA or IIoT network share the same concept of encapsulating the perimeter and not allowing outside connections to business-critical systems. When organizations have to deal with a typical IoT network such as a smart office, they need to make sure that a firewall and an antivirus suite guard against undesired connections and malicious software.
Businesses should always be on alert for unknown vulnerabilities as both SCADA and IoT software and devices have zero-day security holes. Adopting a solution that automatically applies patches and updates solves part of the problem since teams also need to monitor all inbound and outbound connections all the time.
A cybersecurity strategy for protecting SCADA or IoT networks is not a one-time endeavor, teams need to plan carefully what cyber defenses to implement at the very start and then adopt measures to keep threat protection running effectively in the long-term.

Subscribe to Lumifi's Daily Cybersecurity News Curated by a CISO
Date: 01.28 | Time: 1:00 PM MT