- Solutions
- ShieldVision™
- By Use Case
- Industries
- SOC
- Visibility Triad
- Knowledge Center
- Partners
- Company
- Talk to an Expert
Encryption is a method to cypher data that a user sends and receives, as well as data that resides on endpoints and servers.
Any organization must handle Data at Rest and Data in Transit, the former being the data stored on corporate endpoints and servers while Data in Transit representing any message or document employees exchange between offices and with partners and customers.
Email messages make the bulk part of Data in Transit for any organization and securing the content of email messages is not only a matter of common sense but a necessity.
Data protection legislation such as HIPAA, HITECH, Sarbanes-Oxley and GDPR require email encryption to be implemented as a standard business practice across a variety of industry verticals.
Email encryption is the method to turn plain text messages into cipher text that only a person with the appropriate cypher code can decrypt and read upon receipt. Both the email sender and the recipient must share the same encryption key to respectively encrypt and decrypt the message.
A main characteristic of a cyphering code, or algorithm, is to make sure that the email message is unreadable by a third party, even if it falls into the wrong hands. A best-in-class encryption algorithm encrypts your email messages at a level of cyphering that requires many years for a bad actor to decrypt even the simplest message.
Source: Wikimedia Commons
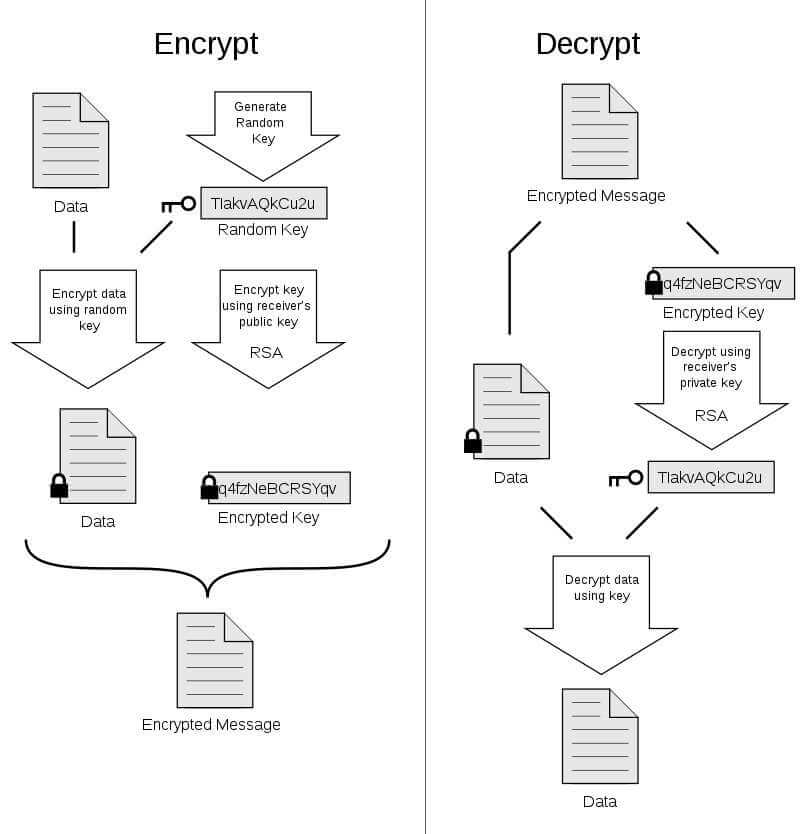
Email encryption works with asymmetric and symmetric keys with both methods offering similar security level but operating in different ways.
A software encrypts the message on the sender’s machine and then the recipient’s machine uses the same encryption key to run a decryption procedure and make the email message readable.
Both symmetric and asymmetric encryption offer an acceptable level of security for the average corporate user while deciding which encryption method requires evaluation of multiple factors involved in complex email encryption and email usage use-case scenarios.
Asymmetric keys used to have a length of 1024 bits before but after several major cyber-security incidents in the past, asymmetric keys now have 2048 bits. A bad actor would need all the computing power now available on Earth and would still need more than 10 billion years to crack an email message cyphered using the RSA asymmetric encryption algorithm, which is widely used to secure business communications.
Symmetric keys also vary in size, but the most common length is 128 bits or 256 bits. Using a secure 256-bit symmetric encryption makes an organization’s communications largely immune to brute force attacks if the encryption key is safe.
Asymmetric keys are bigger and much harder for an attacker to crack the code with which a user encrypts email messages. Encryption feasibility, however, is not only a problem of code’s length but also computational power needed to respectively encrypt and decrypt data. There is also the problem of how to distribute the encryption key to recipients in a way to that keeps them safe.
Symmetric keys are a more bearable computational burden as they are smaller compared to asymmetric keys and still provide an acceptable encryption standard. Encryption is a resource-consuming process. Teams should not underestimate the computing power required to deliver proper email encryption. In this respect, symmetric key has the edge over the use of asymmetric keys.
But symmetric encryption introduces data security risks associated with the exchange of encryption keys between an organization and stakeholders, especially if they reside outside a secure networked perimeter.
Asymmetric encryption eliminates the problem for secure exchange of cyphers by enabling users to freely distribute a public encryption key to anyone and keeping their private key safe within their organization.
Whether to implement symmetric or asymmetric encryption depends on the specific use case and the resources available. Some emailing solutions that use Secure Sockets Layer (SSL) technology for establishing an encrypted link between a mail server and a mail client take advantage of a hybrid cryptosystem that employs both symmetric and asymmetric keys.
Organizations usually deploy a gateway-based method for email encryption, in which a specific software operates on the corporate network and is responsible for encrypting and decrypting email communications.
In a client-based model, an encrypting application is running on the sender’s machine and the sender is responsible for cyphering each email he or she sends.
While the client-based model is more flexible, it requires specific attention from employees who should observe applicable company procedures for encrypting one or another message. The gateway-based model treats each email as sensitive information and applies the chosen method of encryption to every email message.
Regardless of the selected approach toward email encryption, the cyphering software relies on one of three types of encryption to code the email traffic:
An organization will typically deploy a solution that relies on either S/MIME or PGP for email encryption. The S/MIME is a standard developed by RSA Data Security, Inc. and requires an organization to obtain a unique security certificate from a Certificate Authority (CA) or from a public CA.
This email encryption standard secures email communications in terms of authentication, message integrity and non-repudiation. It combines a digital signature with encryption to secure an organization’s email traffic.
PGP and its derivative OpenPGP standard both authenticate the sender of an email message and encrypt the text inside the message body. Using PGP in corporate environment requires a software client running on an endpoint or a plug-in. PGP relies on both public-key cryptography and symmetric key cryptography to deliver authenticated and coded email messages.
Having encrypted email communications is both a matter of securing corporate data flowing over public and private networks and of regulatory compliance.
Securing data flowing through the means of email encryption is mandatory for both small and large organizations operating across multiple industry verticals such as financial services, healthcare, payment processing, e-commerce operations and others.
As organizations often use email to exchange sensitive documents such as financial reports, customer information, contracts, vendor agreements, employee medical information or board meeting minutes, adoption of an email encryption solution is a mandatory part of a wider strategy to both secure crucial communications and protect business-critical data.

Subscribe to Lumifi's Daily Cybersecurity News Curated by a CISO
Date: 01.28 | Time: 1:00 PM MT