- Solutions
- ShieldVision™
- By Use Case
- Industries
- SOC
- Visibility Triad
- Knowledge Center
- Partners
- Company
- Talk to an Expert
A virtual private network (VPN) enables two or more devices to submit and receive data using a secure private connection over a public network such as the Internet.
VPNs use a technology called "tunneling" to establish a secure connection between an organization's network and an outside network through the insecure environment of a public network such as the Internet.
Tunneling is a process that allows a VPN to both encrypt an organization's data in transit and retain its integrity, preventing a man-in-the-middle from reading and changing data packets' content while traveling over a public network. VPN tunneling also enables private browsing by connecting a user to websites through a VPN tunnel.
This connection method, in turn, hides the user's actual IP address and does not reveal the location and computer address to potentially malicious actors monitoring the online space.
A concise definition of VPN tunneling should emphasize that a VPN tunnel creates an encrypted link between a computer or a mobile device and an outside network. Usually, the connection between the two networks occurs over a public network on which data travels unencrypted by default, including the actual data transmitted and meta-data such as the network and computer address, hardware and software identifiers, and other information.
Sharing meta-data with the outside world and transferring unencrypted data is not a safe practice, as it makes users vulnerable to data snooping, man-in-the-middle attacks, and targeted cyber-attacks.
The process of creating and maintaining a VPN tunnel solves the above problems by hiding the actual IP address, encrypting the data users exchange with an outside network, and transporting it securely using methods to re-packet data in transit.
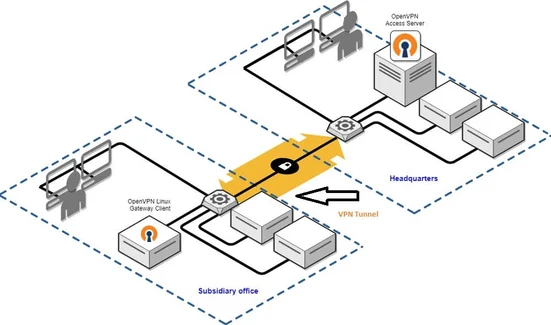
As the diagram shows, a VPN tunnel is a communications concept rather than an engineering method to connect two remote machines using specific hardware and software.
VPN tunneling is a method whose core concept is the encapsulation of data to insulate data packets from other data in the transfer over a network while making the data unusable to unauthorized third parties by encrypting it. Data encapsulation also works as a method to make data packets look like any unencrypted data sent over the Internet and thus avoid unnecessary attention.
Organizations cannot have a physical VPN tunnel as it uses the same IT infrastructure they are using for other networking purposes. Instead, they must employ hardware, software, and encryption technologies to work together in transmitting data over a network and between two locations.
The two main concepts behind VPN tunnels are data encapsulation and data encryption.
Encapsulation and encryption can work on a single machine and without connection to an outside network. When a user comes to the point of transmitting encapsulated and encrypted data packets, they need network protocols to carry data over the network.
VPN tunneling utilizes many protocols that are not equally efficient in securing your data traveling over a public network, however.
Protocols such as Point-to-Point Tunneling Protocol (PPTP), Layer 2 Tunneling Protocol (L2TP)/Internet Protocol Security (IPSec) and Internet Key Exchange (IKEv2)/Internet Protocol Security (IPSec) are all protocols widely used for tunneling. They are considered slightly outdated and offer less security as compared to a few other network protocols.
Secure Socket Tunneling Protocol (SSTP) and OpenVPN protocol are considered the most secure protocols for building VPN tunnels that are available to the public.
Once an organization agrees on the protocol to use for VPN tunneling, they need to establish a model for initiating a VPN connection. They can select between two main types of VPN tunneling, which are known as 'Voluntary' and 'Compulsory' tunneling.
The choice of a network protocol and connection method for VPN tunneling depends on the specific use-case scenario, but in any case, organizations need to have reliable encryption algorithms in place and adopt measures to enforce the use of a VPN connection.
Conclusion
The concept of VPN tunneling depends on an organization's choice of network protocol to transfer your data in a secure manner and the ability to hide their digital address and configuration details.
Current cybersecurity practices show SSTP protocol and OpenVPN protocols provide high-grade encryption and secure data transfers in the context of a VPN tunnel. OpenVPN network protocol is open source, which allows for fast identification and remediation of possible bugs and vulnerabilities while both SSTP and OpenVPN are hard to block by third parties.
Finally, organizations should be aware that VPN tunneling is efficient only in combination with a resilient cybersecurity strategy that includes managed detection and response, endpoint monitoring, and threat intelligence to combat the corruption of end-user machines.

Subscribe to Lumifi's Daily Cybersecurity News Curated by a CISO
Date: 01.28 | Time: 1:00 PM MT