- Solutions
- ShieldVision™
- By Use Case
- Industries
- SOC
- Visibility Triad
- Knowledge Center
- Partners
- Company
- Talk to an Expert
Contrary to popular beliefs, an insider threat is not always a security risk within an organization's immediate perimeter. Current employees and managers aside, an insider threat could be a former employee who had access to specific information, a third-party consultant, or a business partner.
In any case, malicious insiders account for about 38 percent of cyber breaches worldwide between 2012 and 2017, according to statistical reports.
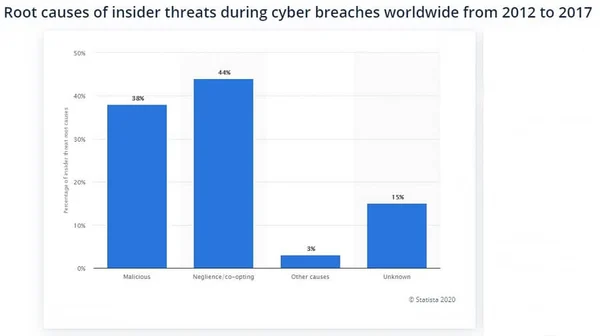
Malicious and cooperative insiders, combined with negligence, are at the core of 81 percent of all data breaches cases during the period, which makes insider threats the top cause of cybersecurity breaches across organizations of all sizes and all industry verticals.
Industry research shows that close to 20 percent of all employees have access to all sensitive data within an organization, which means anyone who knows how an organization's network resources and IT ecosystem works is a potential insider threat. It is even more true for individuals who have, or had, access to sensitive corporate data and know where it resides and what data protection is in place.
The average overall cost of a cybersecurity breach due to an insider threat stands at $11.45 million, according to the Cost of Insider Threats 2020 report by IBM. Thus, insider threats and ransomware emerge as one of the most severe cyber threats organizations face on a global scale.
While preventing insiders from siphoning out sensitive information is a very demanding challenge, there are methods to mitigate the risks associated with malicious and cooperative insiders and detect suspicious or abnormal behavior that indicates an insider may be attacking an organization's business-critical systems and sensitive data.
We should highlight that an overwhelming 62 percent of insider threats are related to data exfiltration, followed by misuse of access privileges with 19 percent. Thus, insider threats are mostly about accessing data and systems and then siphoning out the respective databases or sensitive files.
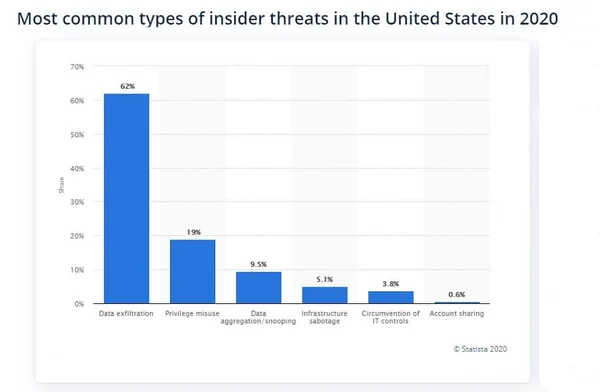
There are two major types of insider threats at the top-level: intentional or malicious insiders and unintentional ones. Unintentional insider threats are generally categorized as 'Pawns' while malicious insiders are 'Turncloaks.' We can further categorize those two types into at least four individual categories of insider threats:
Any employee can turn into a pawn by clicking on a malicious link in a corporate email or making another mistake that enables a bad actor to penetrate the organization's perimeter. Other pawns are victims of advanced hacking tactics that involve social engineering to trick a person into visiting a malicious website or sharing credentials with a bad actor.
Any insider who is stealing data or securing access to systems for a third party is a turncloak. A turncloak has legitimate access to corporate networks, data storage systems, endpoints, and cloud-based systems.
Goofs are not exactly malicious insiders but do not follow the security rules and policies, resulting in more significant cybersecurity risks. Employees trying to bypass the established procedures for access to data or connected systems fall into this category, and they are the main insider threat risk, with over half of all insider threat incidents occurring due to negligence or ignorant behavior by in-house users.
As opposed to a goof, a collaborator is a malicious insider who intentionally steals data or sabotages an organization's operations. Most insider threat collaborators work in cooperation with or under the influence of competitors or nation-state actors, looking for sensitive data and access to critical business systems.
A lone wolf performs his malicious work without being in collaboration with any third party. The lone wolf deliberately steals information or sabotages its operations without being manipulated or otherwise forced by a third party.
Whatever the root cause for such a malicious behavior might be, organizations can look for insider threat behavior patterns and clear signs that a user is acting as a harmful insider.
Indicators of possible insider threat activity fail into two categories: digital warning signs and behavioral abnormalities.
Digital warning signs are far more reliable when analyzing insider threat risks and detecting abnormal behavior. Nonetheless, managers can consider behavior prediction theories to help an organization detect insider threats at an early stage.
None of these theories is a silver bullet to detect insider threats, but a combination of practices and methods used by each theory may prove an excellent tool for preventing some typical insider threats from occurring.
Behavior prediction theories can be of help in avoiding creating circumstances resulting in increased insider threat levels. However, an organization needs to be prepared to deal with insider threats, both preemptively and to be prepared to provide an adequate response to any cases of malicious insider actions.
The fight with insider threats starts with the initial hiring interviews. Organizations need to create a healthy work environment that minimizes the risks of malicious insider behavior and educates their employees to avoid becoming unintentional insider threats or pawns.
Other countermeasures may include:
The abovementioned techniques and methods are the building blocks of a broader framework to deal with insider threats and other cybersecurity risks and involves multiple cybersecurity tools.
Insider threats do not exist in a vacuum, and organizations should address the risks associated with bad insiders along with a plethora of other cybersecurity risks concerning malicious software, Denial of Service attacks, ransomware targeting corporate machines, and any other threats.
Organizations can take advantage of five categories of tools to mitigate the risks associated with cyber threats and insider threats, including:
Whatever a tool or combination of tools an organization may deploy, the focus should be on adopting data-centric and not system-centric cybersecurity.
Every organization should be creating and running a program to counter insider threats while adopting a security policy to mitigate insider threat risks and other major cybersecurity threats.
A combination of thoughtful implementation of behavior prediction theories and the adoption of tools to detect digital warning signs is optimal. Adopting a basic insider threat protection program is affordable even for small organizations, while it is a major prerequisite for sustainable IT security in an environment in which every employee is a potential insider threat.

Subscribe to Lumifi's Daily Cybersecurity News Curated by a CISO
Date: 01.28 | Time: 1:00 PM MT