- Solutions
- ShieldVision™
- By Use Case
- Industries
- SOC
- Visibility Triad
- Knowledge Center
- Partners
- Company
- Talk to an Expert
Biometrics 101
Biometrics utilize your physical characteristics to assess identification matters such as fingerprint scans, facial recognition, retina scans, etc. as a more advanced sector of security. Biometrics is simply defined as a biological measurement or a unique physical characteristic that not even your twin would share. Think of it as you, yourself, being the password.
The biometrics industry has experienced massive growth and momentum over the last decade as more and more cyber-attacks have placed companies in a position to think through more advanced, alternative security measures such as biometric identification. Totaling upwards of $68 Billion in just five years, this industry doesn’t show signs of slowing.
Let’s dive deeper into the benefits but also the potential hidden dangers of biometrics in cybersecurity.
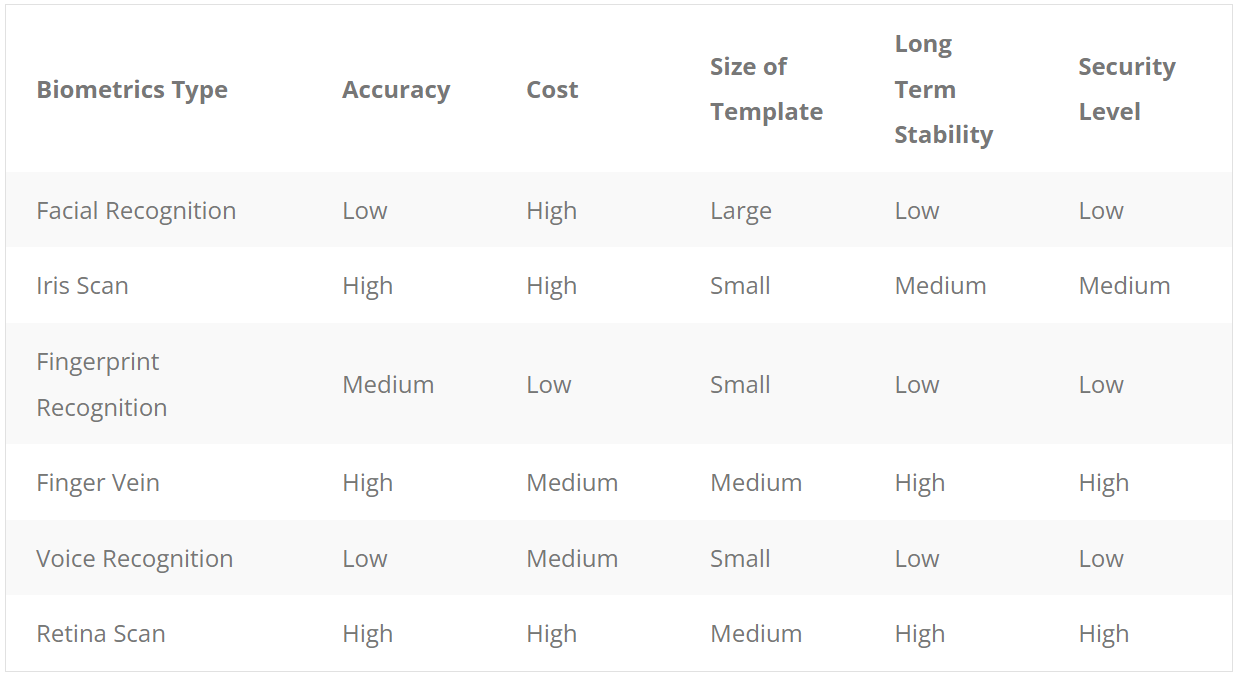
Three Types of Biometric Security
Biometric security can be grouped into three main subcategories such as:
Biological biometrics are exactly what they sound; using your biological makeup to use as identifiers for security purposes such as your DNA, tested through fluid samples.
Morphological biometrics are most commonly used via your laptops, phones, tablets, etc. which include your physical traits like fingerprints and eye/facial shape, which are mapped through different types of security scanners.
Behavioral biometrics include your walk, speech, and other purely behavioral traits exhibited on a daily basis that give way to succinct patterns. Similar to how interrogators use small microaggressions such as the twitch of a nose, or the quiver of a lip for hints of false testimony.
Examples of Biometric Security
While there are many different forms, here are some more common examples:
Odds are, you have run into many, if not all these biometrics at one point or another, whether that be at the hospital or just using an electronic device. Biometric security can be used in a plethora of different applications from a simple fingerprint scan to access a phone, to the protection of nuclear systems via multiple advanced biometrics such as retina/iris scans.
Biometrics has seen a stratospheric rise in adoption over many different industries recently, such as:
While the adoption rates rise, the costs begin to drop for biometrics as to allow mid to small business use and even individual applications are being seen in the market. In days past, only the most high-end phones were equipped with fingerprint scanners but now even the $75 models come fully equipped with this setup. Biometrics are becoming an integral part of everyday life and it seems only inevitable that most businesses will adopt this ideology as well, even on the smallest scale.
But, Are They Safe?
Passwords are forgotten every day, subsequently, they are changed just as often, but biometrics stay with you for your lifetime and are unable to be “changed”, so does this mean they are foolproof? Well, not exactly, but extremely close.
A biometric such as your handwriting or signature can not be stolen, but it can be learned by someone willing to take the time. Similarly, a physiological biometric like face mapping can be stolen through a photograph or some other illegally obtained means of duplication, while this is just a copy, it could still pose potential issues. Even though these biometrics can, in theory, be “stolen”, that does not mean instant access for your attacker since most systems use what’s called “liveness tests”. These tests help prevent and reject any samples of duplicated information such as fingerprints obtained on a piece of tape, or using a photograph of your target to gain entry.
Many devices and systems have taken extra precautions against the examples listed above; take LG for example. They combine facial and voice recognition along with a heartbeat sensor to ensure a copy of a fingerprint can not be used in the same manner as a live person. The real challenges lie in solely facial scanners which have been successfully tricked by researchers and attackers alike.
Researchers at the University of North Carolina set up an experiment to hack into facial recognition systems by downloading social media images of the volunteers and using them to construct 3D models of their faces, ultimately breaking into 4 out of 5 systems; a 90% success rate.
Cloning fingerprints can be done reliably, cost-effectively, and rather quick as a demonstration at the Black Hat Cybersecurity conference showed duplicating a fingerprint using molding plastic or wax in as little as 10 minutes. Biometrics may be the way of the future, but that certainly does not expel risk.
One more example of that aforementioned risk presented itself after the release of the Iphone 5, when members of the group, Chaos Computer Club, successfully bypassed the new fingerprint scanner by simply photographing the target fingerprint on a glass surface and then using it to unlock the phone. Obviously, technology has well evolved since the Iphone 5’s release, but with that comes the evolution of hackers and attackers hoping to create new ways to slip by these biometric systems.
Biometric Data Security Concerns
The more mainstream adoption of biometrics comes with a few data security concerns attached to it. Cybercriminals aim to get their hands on as much personal data as possible and these biometric systems host exactly the kind of information that attackers seek. In 2015, the US Office of Personnel Management was hacked, exposing upwards of 5.6 million fingerprints of official government employees, essentially leaving their identities unlocked for anyone to steal.
Best practices for storing this type of data result in housing this information on a single device rather than a database no matter the level of encryption, as hackers can breach a system and take any and all data that is not properly secured, whereas breaching a single devices information is much more difficult.
Ways to Protect Biometric Identity
Biometric authentication should not be your sole means of protection as multiple means can dramatically increase the safety of your information, such as “liveness tests” like blinking that aren’t able to be duplicated or machined.
Even more advanced systems have begun implementing add-on features for enhanced security such as age, gender, and height to increase the difficulty of obtaining all of this information legally.
Two-factor authentication layered with biometric initial access can be a powerful combination and one that is recommended for secured internet devices as to lessen vulnerability.
Takeaways on Biometrics
Overall, biometrics continue to dominate the market and look to drastically increase security of systems through combinations of physical/behavioral scans along with other authentication. Utilizing simple, character-based passwords, are becoming a thing of the past as biometric technology continues to evolve.
Do you trust biometrics and the new realm of biometric tech? Let me know in the comments.
Subscribe to Lumifi's Daily Cybersecurity News Curated by a CISO
Date: 01.28 | Time: 1:00 PM MT