- Solutions
- ShieldVision™
- By Use Case
- Industries
- SOC
- Visibility Triad
- Knowledge Center
- Partners
- Company
- Talk to an Expert
If there is one broad theme to Verizon's 2023 Data Breach Report, it's that the arms race between cybercriminals and cybersecurity professionals hinges on the human element more than ever. The report declares this clearly in its opening summary, saying that:
Cybersecurity professionals are once again under pressure to adapt to a changing threat landscape. We've gone through Verizon's data and identified five core points security leaders need to internalize to guarantee consistent security performance moving forward.
Internal errors make up a small but significant number of overall breaches covered in Verizon's report. However, these security incidents have a much lower rate of disclosure than external cyberattacks.
This isn't necessarily because security leaders intentionally try to cover up these errors – although some certainly do. It's also connected to the fact that many security teams simply don't have the visibility necessary to detect and respond to these kinds of incidents, whether they result in a breach or not. When internal errors go unnoticed, it's impossible for security leaders to meaningfully address them.
The majority of internal errors come in three distinct flavors:
Not all internal errors lead directly to data breaches. However, organizations that can't detect and rectify these errors practically guarantee that at some point, sensitive data will end up in the wrong hands.
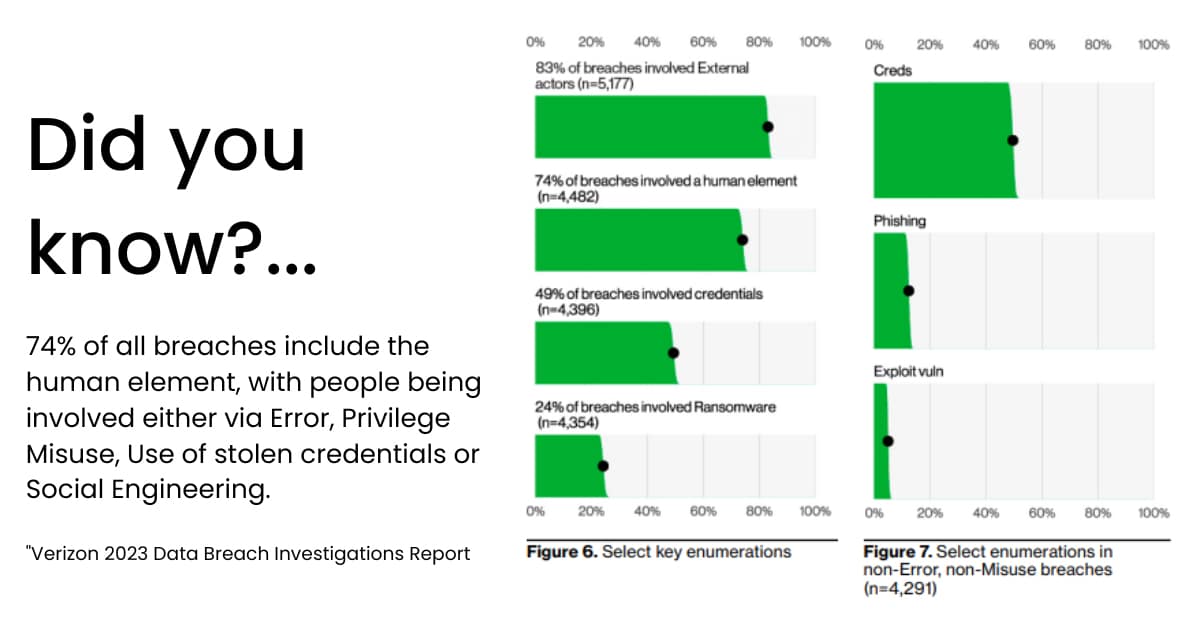
Nearly a quarter of data breaches involve a ransomware step. The idea of a "ransomware step" is an important departure from the traditional categorization of "ransomware attacks" as being different from other types of cyberattacks.
Now, cybercriminals are more likely to build complex, multi-tiered attack strategies where ransomware is just one of many ways they attempt to monetize stolen data.
For example, if security teams successfully repel a ransomware attack with a secure backup system, cybercriminals may simply switch tactics, threatening to leak sensitive data unless they are paid. They may even go further, leveraging the data itself to compromise credentials, attack users, or target third-party partners.
This means that ransomware is still a major threat, even to organizations with anti-ransomware defenses in place. Organizations of all sizes and industries can easily find themselves targeted by ransomware attacks and may be surprised to discover that the story doesn't end when the initial attack is remediated.
According to the report, email is the top action vector for ransomware delivery, followed closely by desktop-sharing software and web applications. Together, these three account for roughly three-fourths of all ransomware attacks.
Even organizations with robust ransomware protection can still find themselves targeted by attackers infiltrating email, remote desktop software, and web applications. If cybercriminals can't monetize the data one way, they'll simply try another.
Privilege misuse includes malicious insiders, and a significant number of these breaches involve multiple threat actors. Specifically, data breaches that combine privilege misuse with fraudulent transactions have surged in the past year.
These findings suggest that cybercriminals are connecting with insiders and facilitating scams that target the organization in question. In some cases, organized crime groups have high-quality candidates apply to open positions, only to exploit the organization months or even years later.
These operations span the range from elaborate long-term fraud to brazen one-time heists. Sometimes a malicious insider with the right privileges can simply redirect enormous amounts of money to a threat actor-controlled bank account and disappear before the organization notices.
The thread that connects these different attacks is collusion. Often, malicious insiders can't siphon funds away from the organization without an external partner who can launder the money properly. This means that some level of cooperation between internal and external threat actors is necessary.
No organization's onboarding process is perfect. Any employee can be (or turn into) a malicious insider. Deep visibility and comprehensive behavioral analysis offer organizations a way to detect these insiders and stop them before they complete their attacks.
Financial motivations are behind nearly 95% of all data breaches, which is in line with previous years. Espionage (either corporate or state-affiliated) is a far second. At the same time, organized crime groups are behind the majority of data breaches, which implies there is still good money to be made in cybercrime.
This finding also puts pressure on organizations to pay greater attention to information security. While most organizations have made great progress in the last few years, it's clear there is still a long way to go.
Several different factors may be holding organizations back from achieving true operational security excellence:
To successfully attribute value to security initiatives, leaders need accurate, in-depth data about how those initiatives impact the organization's top and bottom lines. They must also improve policies by observing how individual users interact with them.
Stolen credentials offer cybercriminals the fastest, easiest, and most effective path of entry into target networks. Roughly half of all breaches start with a compromised credential, compared to the 5% that originate with exploited technical vulnerabilities.
This finding should lead security leaders to reconsider their overall risk management strategies. It should especially concern leaders at enterprise-level organizations where employees hold a large number of software and vendor accounts.
It should also play an important role in strategic decisions about implementing security technologies.
That's because many security providers focus intently on countering the latest technical exploits, even though there are relatively few cybercriminals capable of exploiting these kinds of vulnerabilities on a significant scale.
On the other hand, exploiting a known password may take no technical skill whatsoever. Upon infiltrating the network this way, an insider may be able to do much more damage than a technical cybercriminal who leaves a more comprehensive audit trail.
It can be helpful to look at the way tech companies have historically treated their intellectual properties. They entrust engineers, scientists, and other employees to work with these assets, but act swiftly when it looks like an employee is getting ready to patent a company invention under their own name.
Every organization needs robust identification and authentication policies, but that's not all. Security professionals need to be able to see how authenticated users interact with company assets and flag suspicious events even when the users involved have all the right permissions.
While security leaders are right to be concerned about phishing and technical exploits, credential-based attacks are at the top of the security leader's priority list. Detecting and mitigating credential-based attacks requires carefully monitoring the way human users interact with company assets. This can't be done without deep visibility into how individual users behave on a day-to-day basis.
Lumifi specializes in deploying solutions that grant unlimited visibility into security processes and performance for every user, asset, and entity on the network. Discover how our SIEM expertise can help your organization move beyond compliance and establish a truly robust security posture that will protect it against sophisticated internal and external threats.
Subscribe to Lumifi's Daily Cybersecurity News Curated by a CISO
Date: 01.28 | Time: 1:00 PM MT