- Solutions
- ShieldVision™
- By Use Case
- Industries
- SOC
- Visibility Triad
- Knowledge Center
- Partners
- Company
- Talk to an Expert
Multi-factor authentication (MFA) is a method and technology to verify a user’s identity requiring two or more credential category types for the user to be able to log into a system or make a transaction.
The MFA method requires a successful combination of at least two independent credentials, which generally combines one of three following credential categories:
Note: Multi-factor authentication is only not limited to protecting computing devices, networks or databases.
The ultimate goal of multi-factor authentication is to provide layered security so if an unauthorized person can breach the first layer of defense, or if it is compromised, the penetrator still has one or more additional barriers to breach to enter his digital or physical target.
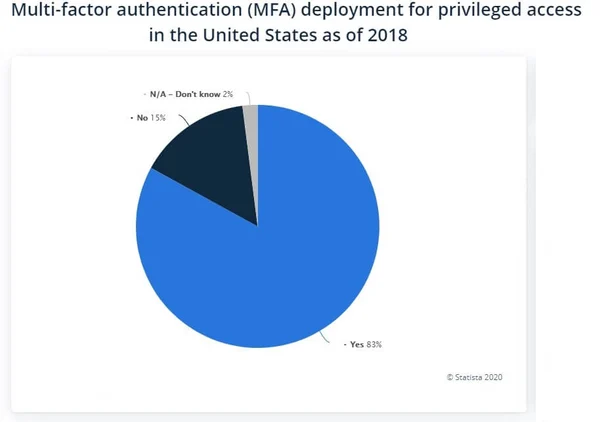
MFA is growing in popularity with 83 percent of respondents in a recent survey across the United States saying their company is using a sort of multi-factor authentication to validate access credentials.
As malicious actors are becoming increasingly adept at breaking single passwords using computers with vast computing power, the need for introducing multilayered security measures becomes a standard. Multiple MFA tools are available on the market, offering a variety of options and methods to protect digital systems and physical locations.
It is impossible to list and compare all MFA solutions available since there are many specialized offerings, but the most popular MFA solutions we review below provide most basic functionality for businesses.
LastPass is probably the most popular multi-factor authentication solution on the market due to its free version for anyone to securely store their passwords and credentials across devices (computers, mobile phones, tablets, etc.).
The LastPass MFA platform combines biometric and contextual factors providing a password-less experience across devices. The authenticator app automatically verifies user identity and no code is required to enter the system a user wants to log into. This way, a user does not need to go through a complicated authentication process as with some other MFA applications.
Organizations can secure cloud-based and on-premise applications, workstations and virtual private networks (VPNs) while various MFA methods are available at user, group and organizational level.
Administrators can take advantage of automated user provisioning utilizing user directories such as Microsoft AD and Microsoft Azure.
Biometric data remains private and secure, as it never leaves a user’s device while being encrypted at device level.
Duo Security, acquired by Cisco in 2018, provides an MFA solution that is based on zero-trust philosophy and utilizes a variety of authentication methods.
Duo offers a mobile app, which allows users to approve or deny any login attempt. Their MFA solution integrates with universal second factor authentication tokens and hardware tokens as well as mobile passcodes, SMS authentication and biometrics such as face recognition.
The MFA systems is scalable and performs as a gateway that integrates both legacy systems and newly installed IT systems. The systems can be deployed in multi-cloud, hybrid or on-premises environments.
Business can secure Software-as-a-Service apps, custom applications, SSH, VPN clients, Bring-Your-Device computing devices as well as offline devices.
Authy 2FA is a popular authentication app for small and medium enterprises. Their mobile app generates 2FA tokens directly on a device, reducing SMS and voice security issues.
It works automatically on new devices and secures 2FA data by storing and backing up sensitive data in the cloud, without storing passwords with the service provider.
As the security codes are generated on the device itself, users can use it even if they have poor Internet connection and when the device is offline.
Ping Identity offers several cyber security products with PingID MFA being one of the most popular.
PingID is a cloud-based, multi-factor authentication solution that features adaptive authentication policies, which recognize low-risk and high-risk use case scenarios.
The app supports mobile push authentication methods like swipe, tap, fingerprint and facial recognition as well as SMS one-time passcodes (OTP). Authentication in low-risk scenarios utilizes contextual data such as device posture, device management, geolocation, geo-velocity, IP address and IP reputation and last authentication date.
The application best suits the needs of large enterprises, which need adaptive policies across all their applications.
RSA SecurID Access is an enterprise-grade MFA and access management solution, which enables organizations to force dynamic risk-driven access policies across the entire organization.
Their solutions provide support for push notifications, biometrics, one-time passwords and SMS messages. RSA SecurID Access also supports hardware and software tokens.
Users can choose between using token-based authentication or using the mobile app, while the platform is supporting over 500 cloud and on-premise applications.
The applications mitigate security risks by taking automated access decisions based on user-associated risks such a physical location, application sensitivity, device type and other factors. All these risk factors are being evaluated in real time.
Users can deploy the app in the cloud or on-premises, while getting protection for standalone business software and SaaS applications alike.
SecureAuth Identity Platform is available for deployment in the cloud and on-premises and supports hybrid models. Users can choose between nearly 30 MFA options for a variety of use cases.
The application enables system administrators to build various workflow that reflect the respective risk profiles and how sensitive is a specific resource one needs to access.
The authentication process analyzes devices, location, IP Address and behavior, while user identity is being verified when there are doubts about a login attempt.
Silverfort is a unified platform for adaptive multi-factor authentication, which is available as a cloud-based, on-premises and a hybrid solution. It does not require deployment of software agents or gateways and no modifications to endpoint or servers is needed.
Organizations can enforce multi-factor authentication across applications, critical IT infrastructure, IoT devices, healthcare systems, dynamic IaaD environments and databases.
Silverfort relies on an AI-driven risk and trust engine that analyzes all human and machine access requests not only at the perimeter but also within the network.
Auth0 is an online authentication platform offers an impressive free 7,000 users and unlimited logins, as well as custom business plans.
Their easy-to-use MFA solution works with Guardian iOS or an Android app to send push notifications, one-time codes via SMS. It also supports third party token generation apps such as Google Authenticator. Push notifications work on works on devices such as Android Wear or Apple Watch.
Idaptive is an enterprise-grade solution in the cloud, on mobile and on-premises. Their solution is an integrated platform that combines multi-factor authentication, single sign-on, mobility analytics and user behavior analytics.
Authentication methods include push notifications, mobile authenticators, SMS messages, email messages, interactive phone calls and hardware tokens. Derived credentials also help to verify user identity.
Administrators can analyze login requests against historical patterns based on location, device, network and time of access requests, which enables creation of security policies that trigger alerts if they detect anomalous behavior.
Google Authenticator is the most basic authentication app but remains a popular choice for companies.
Organizations can add accounts by scanning a QR code with their phone’s camera or by entering a numerical code.
Users can change phones relatively easy, but the app offers no support for multiple devices or for cloud syncing. The app is available for both iOS and Android smartphones.
Subscribe to Lumifi's Daily Cybersecurity News Curated by a CISO
Date: 01.28 | Time: 1:00 PM MT