- Solutions
- ShieldVision™
- By Use Case
- Industries
- SOC
- Visibility Triad
- Knowledge Center
- Partners
- Company
- Talk to an Expert

Organizations need cyber defense tools to supplement in-house IT security teams.
Phishing and other social engineering attacks are a challenging problem for financial institutions and their customers. Users have long been a weak link in IT security by opening infected email attachments, clicking on malicious links, and communicating with unknown and untrusted sources outside the organization. In recent years, careless employee behaviors have helped spawn a broad range of sophisticated social engineering attacks. They nearly always involve one-to-one interaction between an internal employee and an external attacker who tries to disguise himself as a legitimate, trustworthy business or personal entity. In some cases, the attacks focus on psychological manipulation and behavior modification.
Social engineering attacks have many names, including whaling, baiting, smishing, pretexting, and many more. But perhaps the most common and effective social engineering attack is phishing. These attacks, typically delivered via an email message that appears to be trustworthy, encourage the recipient to do one of three things: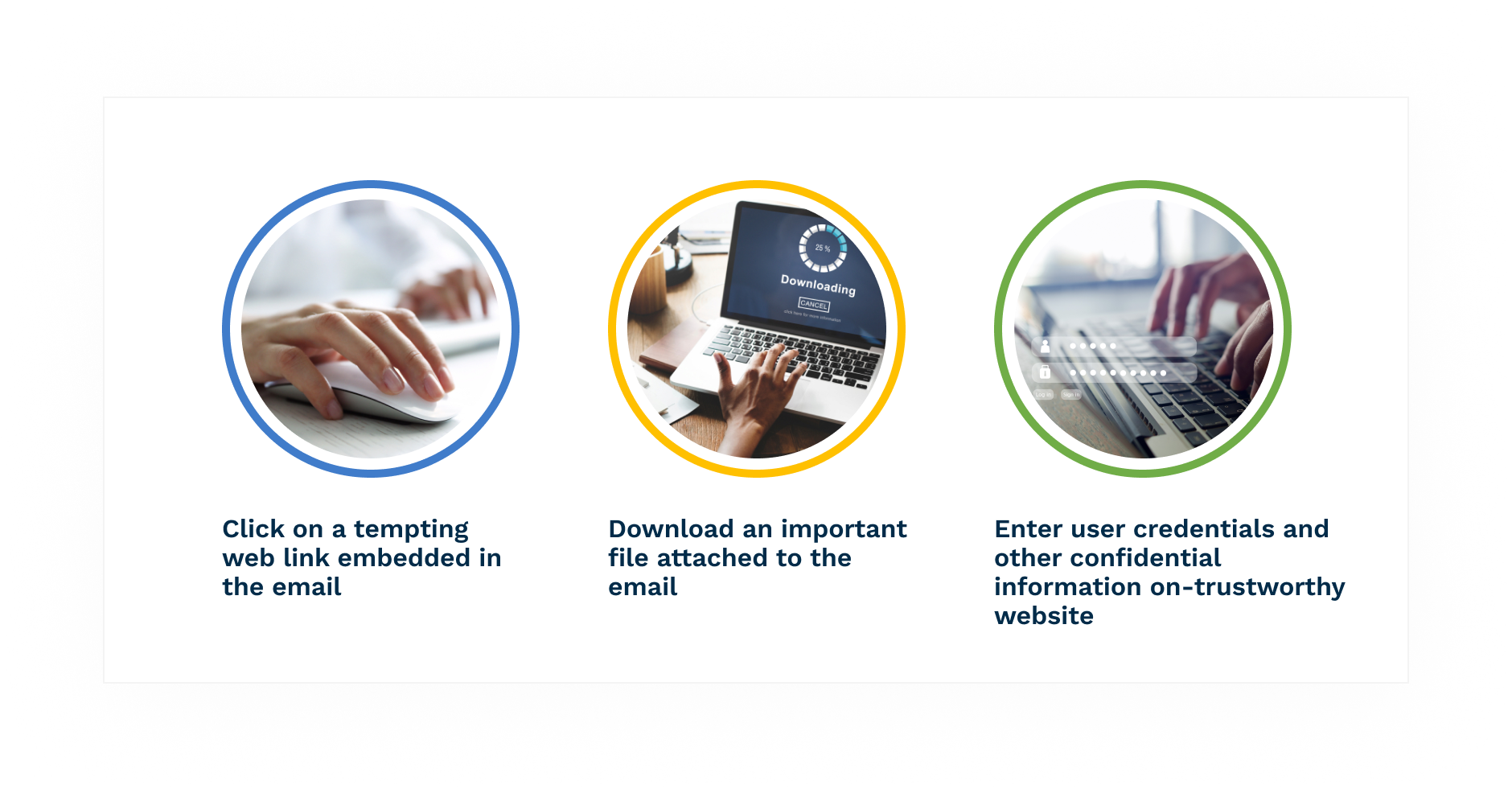
Red flags of potential phishing emails can include misspelled words, a sense of urgency for the recipient to take action, or slight variations of someone' name or title within an organization.
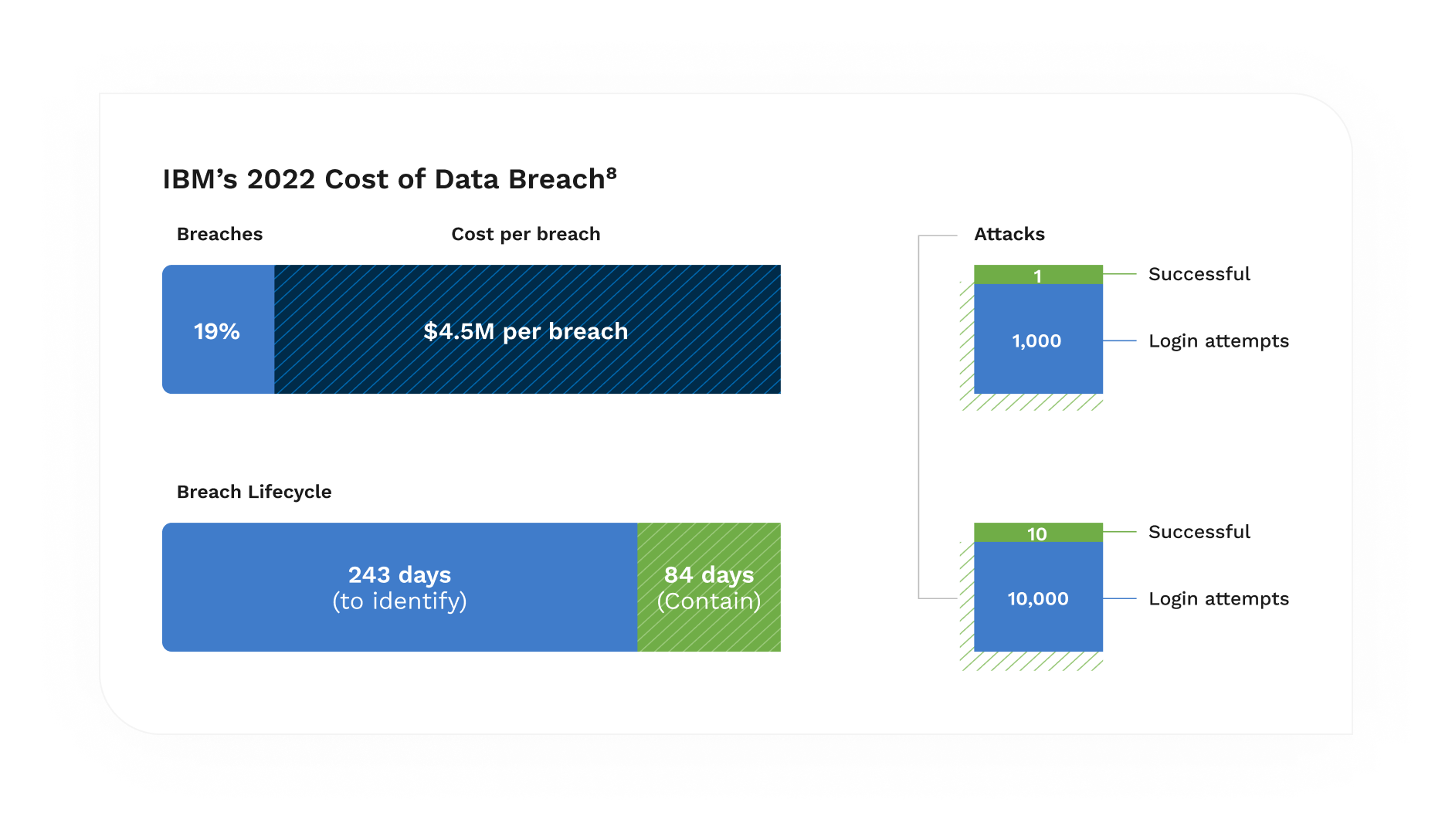
The Ponemon Institute estimates that phishing attacks cost businesses nearly $15 million annually, and that cost appears to be increasing each year. Breaches caused by phishing also took on average 219 days to identify and an additional 76 days to contain, according to IBM.

There were more than 1.2 million total phishing attacks in the third quarter of 2022, according to the Anti-Phishing Working Group. It set a new record and the worst quarter for phishing that APWG has ever observed. The financial institution industry was the most targeted in Q3, representing 23.2% of all phishing attacks.

An even more sophisticated version of phishing is business email compromise (BEC). BEC is one of the fastest-growing, most financially damaging internet-enabled crimes, according to the FBI. BEC actors have targeted large and small companies in all 50 U.S. states and 150 countries around the world.

These attacks begin with a hacker gaining access to legitimate business email accounts to impersonate a company executive or a trusted vendor outside the company. Then, for example, a personal email message from a business contact is sent to a targeted employee inside the company with a seemingly legitimate request for payment, complete with instructions for a wire transfer or check deposit. The scam has progressed to requests for W-2 information, diversion of payroll funds, and fraudulent requests for large amounts of gift cards, according to the FBI.

The pandemic helped cyber criminals carry out their online attacks in sophisticated ways as more workplaces conducted business virtually. They often impersonated vendors and requested payment outside the normal course of business. The Internet Crime Complaint Center (IC3) has also observed the emergence of newer BEC schemes that exploit the reliance on virtual meetings. One example: The bad actors compromise a high-ranking company leader' email to request employees participate in virtual meeting platforms. The fraudster would then insert a photo of the company leader with no audio, or a "deep fake" audio. The bad actor would then claim their audio wasn't working but would instruct employees to initiate wire transfers. It sounds fishy, no pun intended, but remember, these fraudsters often target employees on a lower level who may not have the confidence to question authority.
The FBI also noted that attackers are leveraging BEC schemes to hit municipalities purchasing protective equipment and other supplies related to the pandemic. These emails target anyone who executes legitimate funds transfers. One bank received an email from a supposed customer in China requesting they transfer invoice payments to another bank due to "Coronavirus audits" that had rendered their existing bank accounts inaccessible. The bank realized too late that the email was fraudulent, and the transferred funds were lost.
Cybercriminals are successful in stealing money in other ways too. In a real example from a midsize organization, BEC fraudsters emailed several company employees, appearing to be from their direct manager. The bad actors slightly changed the leader' title in the email signature and used an email address that was different, yet similar to the manager' legitimate email address. Posing as the manager, they told the employees they quickly needed them to go to a store and purchase $1,000 worth of eBay gift cards. A few employees called the manager to verify the odd request and learned it was not legitimate. However, one employee did not verify and went to a local drugstore to purchase the gift cards. She emailed back and forth with the fraudsters the entire time to update them on her status. After the purchase, they told her to scratch off the back to reveal the card number and security code, take a photo of it, then email it. She did so and within minutes, she was out $1,000. Gift card requests were the most popular cash-out method of BEC attacks in Q3 2022, according to the Anti-Phishing Working Group.

Once cybercriminals use phishing tactics to trick users into giving up sensitive data or downloading malware, they can launch a second-phase attack. There is a consistent demand for compromised consumer accounts on dark web marketplaces. Attackers use compromised credentials to attempt access to other accounts. The reason this is so successful is that many people use the same username and password across multiple accounts.

Defending against these types of attacks starts with a cyberdefense that includes employee training, effective identity and access management, and strong email security. Financial institutions should also consider a security assessment service to identify potential vulnerabilities that would allow these attacks to occur. In addition, partnering with an MDR provider could help supplement an organization' security team. It would also bring additional SIEM platform expertise to create a superior defense solution.
Lumifi uses two indispensable cyber threat intelligence tools – Anomali ThreatStream and SentinelOne XDR (extended detection and response) solutions. These tools feed valuable data into the Exabeam SIEM, the platform of choice for our customers, which then validates and scores all threat intel from various sources. SentinelOne XDR, a software solution for threat detection and incident response, provides a 360-degree view into our clients' security landscapes and simplifies investigations. Organizations with XDR technologies identified and contained a breach 29 days faster than those without XDR, according to IBM' Cost of a Data Breach Report 2022.
Financial institutions cannot rely on employee training alone to ward off phishing attempts. They need strong cyber threat intelligence tools to prevent data breaches and protect sensitive information so their organizations do not become victims of fraud.
Lumifi wants to partner with you in your fight against dangerous phishing attacks. Contact us today to learn more about adding detection capabilities to your systems.

Date: 01.28 | Time: 1:00 PM MT