- Solutions
- ShieldVision™
- By Use Case
- Industries
- Compare Us
- SOC
- Visibility Triad
- Knowledge Center
- Partners
- Company
- Talk to an Expert
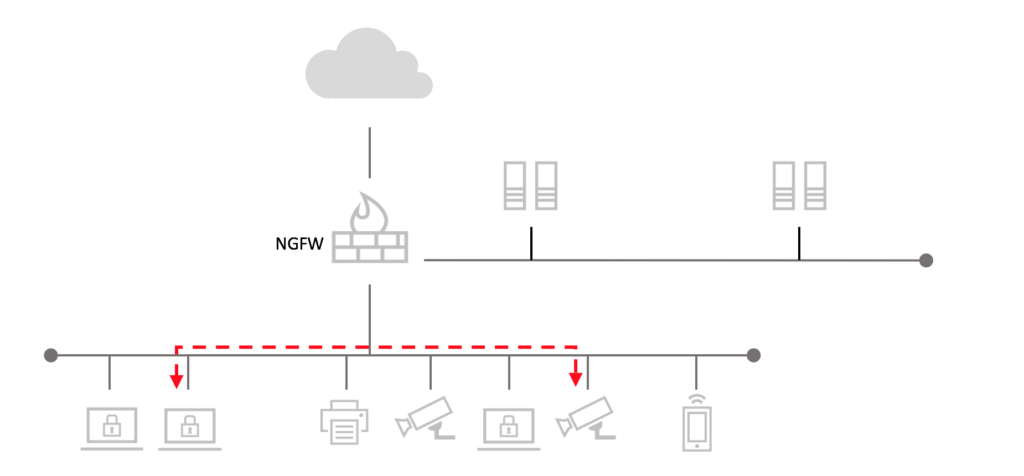
Network segmentation is the practice of dividing a formerly 'flat' network [where every device can contact every other device] into a series of segments that have restricted communication between them.
What's this mean in real terms, though? And why would you want it - and is it useful outside of making PCI compliance easier?
In real terms, this means that you will end up working with your network hardware to create a set of 'zones' or enclaves, populated with a given group of assets. Then, you'll put some kind of barrier between each of these zones - either by assigning each of them to a VLAN and restricting routes between VLANs, or setting up a firewall to partition off various subnets and restrict communications - or a combination of the two.
As an example, consider a small sandwich shop that accepts credit cards. It has some POS terminals at the registers, a back office for management, and offers wifi for the customers.
In this case, you would want a segment for guest wifi - a separate VLAN that only routes out to the internet - to keep guest devices outside of the card processing environment. Similarly, you would want a segment for the POS terminals that can route to the network gateway - for credit card authorization - and for traffic from the registers to the management network - so that management can keep track of inventory sold.
By restricting the kinds of communication that are possible to the kinds that are specifically allowed, you've made your network more secure - the disallowed kinds of communication are either not possible, or require changing the setup in a way that would be very obvious to the SIEM.
Likewise, if you restrict the kind of traffic that can transit between zones to the minimum necessary traffic, any attempts by an attacker who has managed to infiltrate one segment to attack other resources will be restricted, or possibly prevented - and activities taken by the attacker to discern the kinds of assets on the network will be much more obvious.
A side effect of segmentation is that in some instances network performance may be improved. Several different protocols - like NetBIOS - generate broadcast traffic; if this traffic is forbidden from crossing segment boundaries into areas where it is not needed, then the overall amount of traffic on the network can be reduced. With modern networks this is usually not a significant concern, but it can be mildly beneficial in some instances.
Network segmentation also has benefits for compliance - in many cases, if the kinds of traffic that need compliance certification are isolated on a specific segment, that restricts the scope of the audits required to maintain certification to that specific segment. Smaller scopes are easier to audit, and it is easier to prove compliant configurations - you won't need to account for every single asset.
Segmentation is a very worthwhile means of adding to the security posture of your network. Talk to us here at Lumifi about whether your organization would benefit from this kind of defense in depth, and how it can be integrated into your existing security posture; we'd be happy to help.
Subscribe to Lumifi's Daily Cybersecurity News Curated by a CISO
Date: 02.28 | Time: 10:00 AM MT