- Solutions
- ShieldVision™
- By Use Case
- Industries
- SOC
- Visibility Triad
- Knowledge Center
- Partners
- Company
- Talk to an Expert
Traditional SIEMs are based on correlation rules, with no machine learning and no behavioral monitoring. Security teams, and especially SOC Analysts, are under enormous pressure to protect an organization.
While Castra does have a reputation within the industry for generating meaningful value using traditional SIEMs, we invite you to see what we can do with even better tools!
If you speak with the likes of Gartner, they will tell you that logging, UEBA, and SOAR are now the three key components of a modern-day SIEM.
Castra believes that logging is a commodity and that the value of SIEM is in automation and analytics. As such, Exabeam was the first Gartner MQ SIEM leader to disrupt the pricing model of this market.
They did this by launching their SIEM/UEBA/SOAR with a user-based pricing model, as opposed to the volume-based pricing models imposed by the large majority of the industry.
Since Exabeam introduced this model, some traditional SIEM vendors have been forced to respond by introducing their own user-pricing model.
Today, data lakes are popping up everywhere, and organizations need a SIEM that can pull data from many locations – SIEM differentiation will no longer be in the collection and storing of logs, but in the application layer.
In parallel, IoT and OT devices are raising the level of importance of Information Security. As well as monitoring users, laptops, and servers, security teams need to monitor everything IoT that accesses company data or can access company systems, including customers, partners, or vendors (supply chain).
Castra' unique approach as a transparent, integrated, and affordable service provider will ensure all organizations (no matter their size or industry) have a robust and flexible approach to their Security Program.
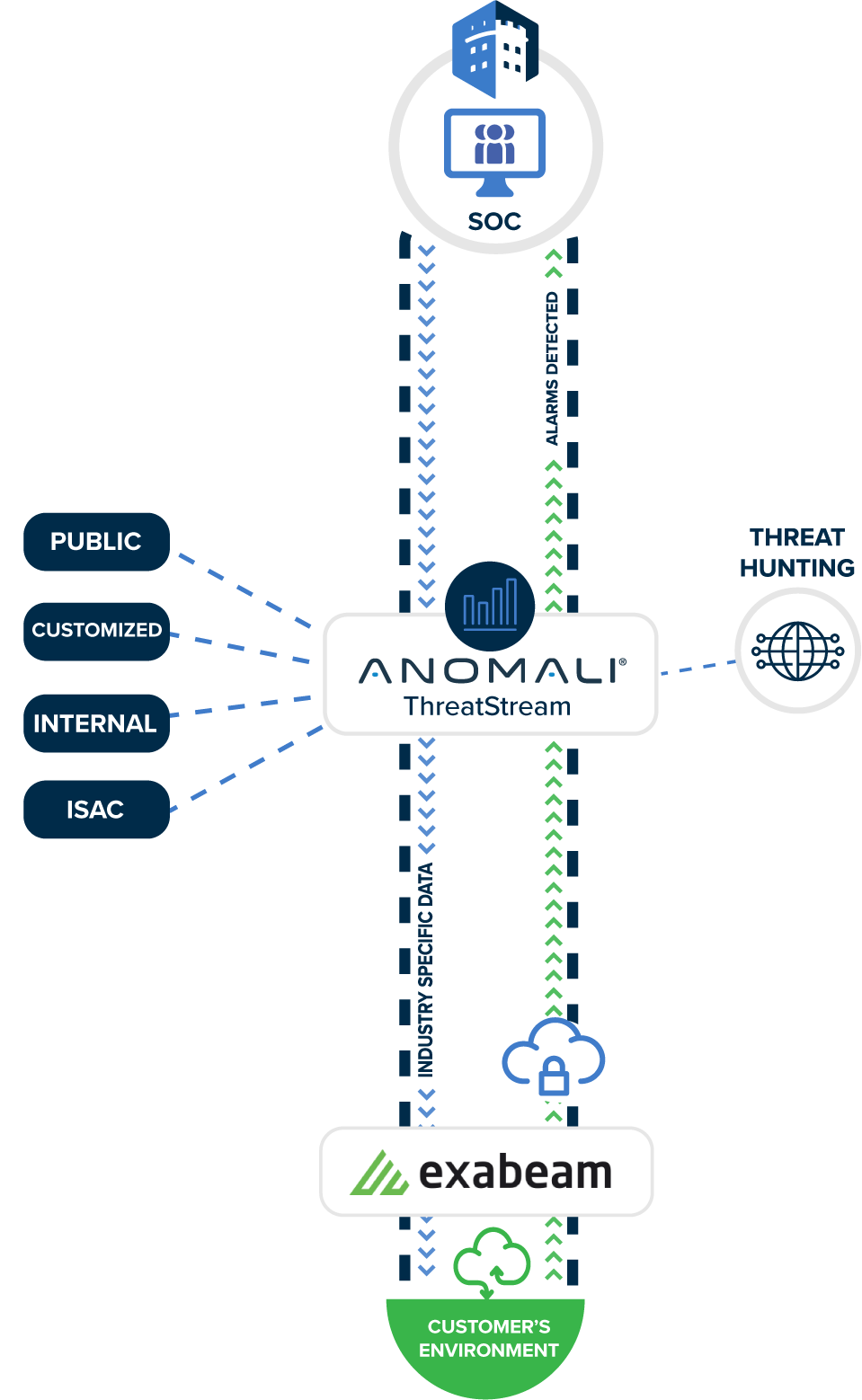
The Exabeam Security Management Platform is a modern SIEM that helps security teams work smarter. Organizations can take advantage of the big data architecture, advanced analytics, and automation capabilities. Exabeam delivery consists of three simple constructs: objects, insights, and actions.
And critically, not only will objects, insights, and actions be available within Exabeam' platform, but they can also be shared with other applications in orchestrated responses.
The platform will include tools to allow Castra engineers to create custom content: parsers to ingest data, IR integrations, and even machine learning (ML) models to improve detection, and playbooks with near-limitless outputs.
Castra will have the ability to add additional applications to the Exabeam platform – playbooks executing on-demand vulnerability scanning or managing cloud security configurations, just to name two.
Each application on the platform can share objects, insights, and actions with Exabeam, and with each other.
Of course, analysts will be able to source data from any repository, be it on-premises or in the cloud. And it is built with the needs of an organization' future in mind: multi-region cloud, scale, automation, reporting, RBAC, HA/DR, archiving, and more.
{{cta('76a936bd-b292-4db6-adac-b836743c4452')}}
This new platform will allow hybrid security operations teams to help reduce risk, time, and exposure:
Exabeam is a leader and visionary in the use of AI and machine learning in its platform, which enables Castra to better detect and respond to all cyber incidents.
Since its inception, Exabeam applied AI and ML to create various techniques to identify adversaries in the customers' environment, looking at behavior amongst peer groups and organizational commonalities.
With AI and ML in Exabeam' Advanced Analytics, the other Exabeam tools, Case Management and Incident Response yields, alert mitigation for analysts that would make their work more efficient by leveraging learned data models and new detection technique attacks spanning multiple MITRE TTPs.
Lastly, Exabeam' strategy is to continue to invest in and foster innovations that would be incorporated into the platform to simplify workflows and provide excellent and automated visibility into customers' technology environments. Below are some specific capabilities in Exabeam to consider:
UEBA can detect security incidents that traditional tools do not see, because they do not conform to predefined correlation rules or attack patterns or because they span multiple organizational systems and data sources.
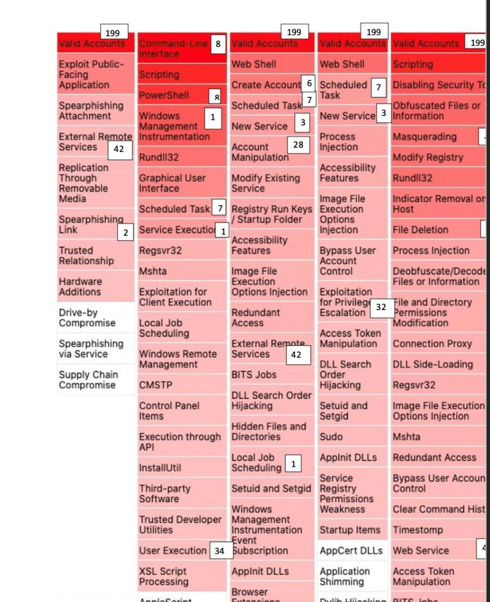
Cyberattacks continue to infiltrate companies at an alarming rate. In just one recent example, we saw Cognizant, a supplier hit by MAZE.
Cybercriminals steal valid credentials to impersonate legitimate users, span IT environments, and conduct malicious activities along the way. Exabeam and Castra can detect the subtle anomalies and correlate them across the complete attack chain, leveraging the existing log repositories to search and scan when detecting malicious behaviors.
Exabeam adds security intelligence to existing log management or data repositories to understand a complete picture of the user' session, allowing the technology to detect and assemble the full attack chain.
The Exabeam User Behavior Intelligence solution uses a powerful combination of session assembly and Stateful User Tracking‚Ñ¢, behavior analysis, and risk-scoring to automatically determine the likelihood of an attack and prioritize responses. Its revolutionary technology focuses on user behavior and minimizes the mundane steps in detecting cyberattacks.
Exabeam Advanced Analytics (or UEBA) is the behavior analysis component of the offering in which Exabeam detects anomalies. Exabeam continuously maintains a baseline of normal behaviors for each user, entity, and each group (e.g., department) within the environment. New activities are then compared to the baseline and reported as anomalies if they are deemed inconsistent.
Exabeam analyzes discrete events to build user sessions from the time a user logs in until the user logs out or the session ends. Exabeam then compares the behavior of each new user session to all previous sessions.
As hosts change IP addresses or users switch credentials, Exabeam is able to intelligently track these changes and attribute these activities to the correct user session.
The Exabeam Security Intelligence platform includes Exabeam Incident Responder (EIR), an incident response automation product. EIR includes a fully customizable incident response management system that can be used to track the status of incidents, gather artifacts and entities, assign ownership of the incident to analysts, and perform investigations.
All fields within this system are fully customizable, allowing security teams to create a response management system that matches their desired workflows and processes. EIR' incident management system is context-aware, and the UI automatically displays different information to users based on the specific type of incident being viewed. For example, phishing incidents will show information about senders, recipients, and subject lines, whereas malware incidents would show fields related to hosts, malware names, attacker URLs, and so forth.
Subscribe to Lumifi's Daily Cybersecurity News Curated by a CISO
Date: 01.28 | Time: 1:00 PM MT