- Solutions
- ShieldVision™
- By Use Case
- Industries
- SOC
- Visibility Triad
- Knowledge Center
- Partners
- Company
- Talk to an Expert
In our experience, incorrect/empty logs or lack of logging required for advanced detection (as we discussed in the first post on this topic), is obviously bad, yet failing to pick them up and sticking to collecting in just System, Security, Application leaves machine learning and modeling missing key items to with which to model behavior.
Beyond the basic logging configured in the previous blog, we will also need to be collecting these Powershell logs from these locations:
WMI-Activity/Operational Logs
Microsoft-Windows- WinRM/Operational
PowerShell/Operational Logs
Windows PowerShell Logs
Many systems use NXlog to transmit logs back to a SIEM, though the examples below can be translated into OSquery as well. Further down we will use examples for Exabeam.
A basic input section for an NXlog config might look simple like this:
##
## Inputs:
##
## Windows event log:
<Input in_windows_events>
Module im_msvistalog
SavePos FALSE
ReadFromLast TRUE
Query <QueryList>\
<Query Id="0">\
<Select Path="Security">*</Select>\
<Select Path="System">*</Select>\
<Select Path="Application">*</Select>\
<Select Path="Windows Powershell>*</Select>\
</Query>\
</QueryList>
</Input>
But with a quick edit we can grab the additional logs we need:
##
## Inputs:
##
## Windows event log:
## Additions
## WMI-Activity/Operational Logs
## Microsoft-Windows- WinRM/Operational
## PowerShell/Operational Logs
## Windows PowerShell Logs (focused option and all option below, choose one)
<Input in_windows_events>
Module im_msvistalog
SavePos FALSE
ReadFromLast TRUE
Query <QueryList>\
<Query Id="0">\
<Select Path="Security">*</Select>\
<Select Path="System">*</Select>\
<Select Path="Application">*</Select>\
<Select Path="Microsoft-Windows-WMI-Activity/Operational">*[System[(Level=1 or Level=2 or Level=3 or Level=4 or Level=0) and ( (EventID >= 5857 and EventID <= 5861) )]]</Select>\
<Select Path="Microsoft-Windows-WinRM/Operational">*[System[(Level=1 or Level=2 or Level=3 or Level=4 or Level=0) and (EventID=6 or EventID=8 or EventID=15 or EventID=16 or EventID=33 or EventID=91 or EventID=168)]]</Select>\
<Select Path="Microsoft-Windows-PowerShell/Operational">*[System[(Level=1 or Level=2 or Level=3 or Level=4 or Level=0) and (EventID=4103 or EventID=4104 or EventID=8193 or EventID=8194 or EventID=8197 or EventID=40961 or EventID=40962 or EventID=53504)]]</Select>\
<Select Path="Windows PowerShell">*[System[(Level=1 or Level=2 or Level=3 or Level=4 or Level=0) and (EventID=400 or EventID=403 or EventID=800)]]</Select>\
<Select Path="Windows Powershell>*</Select>\
</Query>\
</QueryList>
</Input>
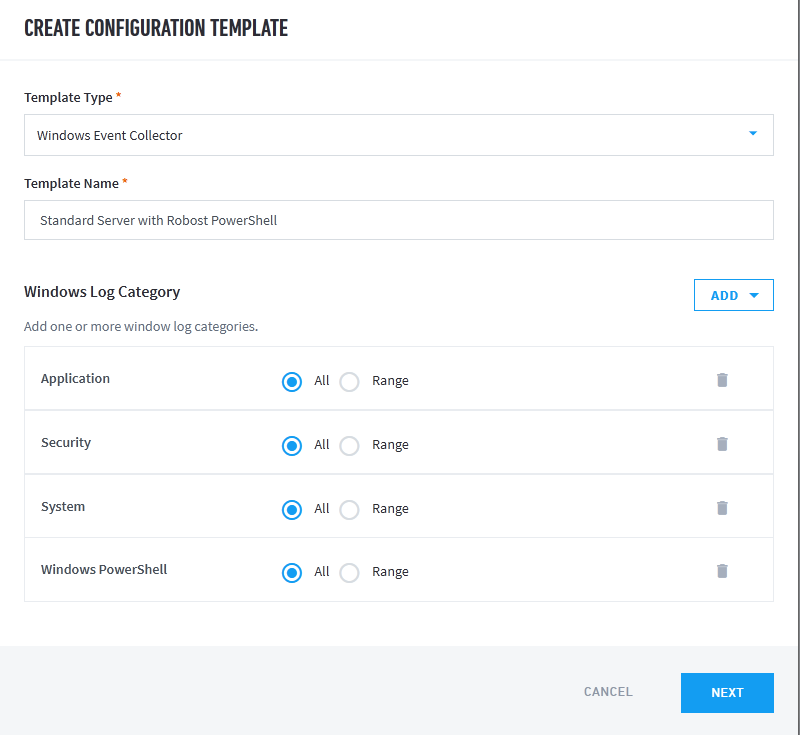
Here, I just added the 3 new channels for PowerShell:
## WMI-Activity/Operational Logs
## Microsoft-Windows- WinRM/Operational
## PowerShell/Operational Logs
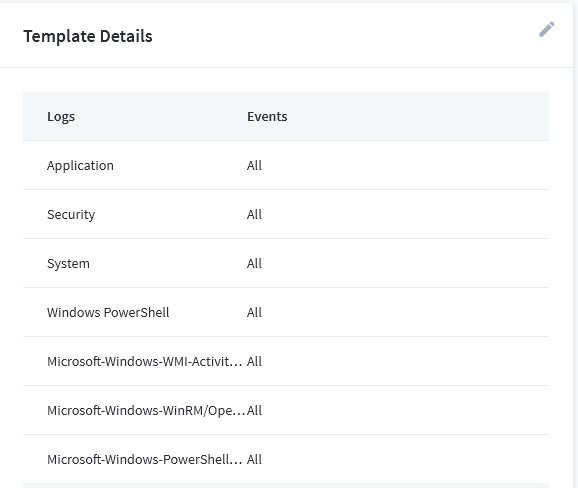
This allows us to collect PowerShell logs that help show encrypted channeling, encrypted arguments in a command, hidden arguments in a command, hiding PowerShell history in a PSReadLine, and more! We will get into writing those rules in our next blog.

Subscribe to Lumifi's Daily Cybersecurity News Curated by a CISO
We’ve expanded our MDR capabilities with enhanced incident response and security services to better protect against evolving cyber threats.