- Solutions
- ShieldVision™
- By Use Case
- Industries
- SOC
- Visibility Triad
- Knowledge Center
- Partners
- Company
- Talk to an Expert
Dealing with credential harvesters has its perks. Day in and day out I get to personally observe how sophisticated a phishing website can be.
Some websites are so elaborate that only a trained analyst can identify them, while others are so obvious no one in their right mind would fall for it. Either way, if it looks suspicious just follow the “POST”.
The “POST” method is one of the many ways the HTTP protocol sends data. The “POST” method is used to submit data to the webserver, which is commonly used to modify a change in state on the server. This is frequently used when logging into your account on another website.
Knowing this, and the using the ingenious “Network” resource in your browser, you can see where you are sending that “POST” request, or more likely, what credential harvester you are giving your username and password to.
Recently, Lumifi's ASOC investigated a credential harvester infrastructure set up by a malicious actor who forgot to use ACLs (Access Control Lists) on their webserver. Because they neglected implementing this important security feature, we were able to navigate backwards through the webserver directories to discover a text file containing a large repository of submitted credentials.
** All data shown below has been sanitized. See the end of the article for a full list of all artifacts that have been changed.
The reported email:
While reviewing the email, it was identified that the sender (chuck.mallory[@]gmail[.]com) tried to convince the recipient (alice.faythe[@]outlook[.]com) that they missed a phone call and a voicemail is ready for them to listen to if they click on an embedded link.
Embedded link: hXXps://sub-domain[.]badguydomain[.]com/page/index[.]html#alice[.]faythe[@]outlook[.]com
The Initial email received:

Accessing the phishing site
Once we clicked on the link in our sandbox environment, our browser opened and went to a credential harvesting website masquerading as an Outlook login page. Viewing the URL in the browser, we can see that it is not a domain associated with Microsoft. Knowing this, we used Mozilla’s developer tools by clicking the “F12” key and then clicked the Network tab. Instead of using the recipient’s email (which can be seen in the URL), I used an email address that had no association to the recipient’s address and entered in a fake password. After selecting the “sign in” option, the browser then sent multiple GET requests to badguydomain[.]com. However, there was one POST request that was sent to a different domain credential[.]dumping[.]com.
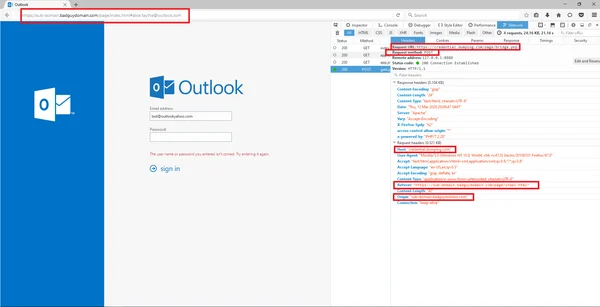
Accessing the credential dumping site
With this HTTP request being observed, we decided to go directly to the webpage hXXps://credential[.]dumping[.]com/page/bridge[.]php.
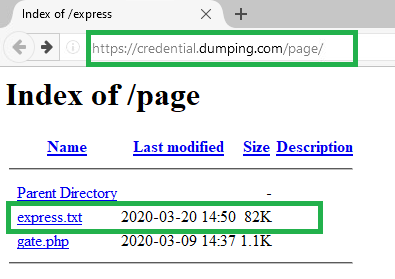
The webpage presented a blank webpage with no information. I then decided to work backwards through the webserver directories to identify what shares are left open for external users to view. Fortunately, the threat actor failed to secure what shares and files the public can access.
The list of submitted credentials
After clicking on “express.txt”, I could see all the credentials that were captured. This allowed me to identify and notify our customers and some non customers of the compromised email accounts.

This also allowed us to investigate further to see what clients made POST requests to credential[.]dumping[.]com. We then made the appropriate containment and eradication steps by having the affected accounts’ passwords changed, blocked both the credential harvester and the credential dumping site, and finally removed email from all mailboxes.
List of affected email accounts. All told, more than 400 accounts were in this list.
Credential Harvesting Lessons Learned
This is just one of many standard investigation procedures we follow at Lumifi. We pride ourselves on not only identifying threat vectors but investigating thoroughly to discover any and all resources a threat actor may use against a victim. Occasionally, as seen above, this can lead to interesting discoveries and meaningful insights.
Are you interested in Lumifi's threat analysis and ASOC capabilities?
Contact Us Today
**Please see the list of edited items below:
- Senders email address
- Recipients email address
- Details in the email
- Credential harvesting domain
- Submitted credentials domain
- List of affected email accounts, password, location, and IP

Subscribe to Lumifi's Daily Cybersecurity News Curated by a CISO
Date: 01.28 | Time: 1:00 PM MT