- Solutions
- ShieldVision™
- By Use Case
- Industries
- SOC
- Visibility Triad
- Knowledge Center
- Partners
- Company
- Talk to an Expert
(Updated May 2022)
Filters are one of the fundamental tools of information security. Firewalls use them to separate suspicious inbound traffic from the flow of data throughout your organization. SIEMs use them to categorize log data and put high-priority alerts above false positives.
These are some of the best-known use cases for filtering data, but they aren't the only ones. Egress filtering is not as obvious, but it' an important part of the in-depth defense that modern enterprises need to adapt.
Egress filtering tools control how traffic flows from the inside of your network to the outside. This kind of outflow control can play a vital role in your overall cybersecurity posture. This role is often subtle, but it' important nonetheless.
Egress filtering adds an additional layer of defense to your overall security posture. When set up correctly, it can provide valuable data about what' happening in your network and right up to the network edge.
For example, cybercriminals can scan outgoing traffic for information about how your network is structured and what systems are active on it. NetBios data could indicate what kinds of devices exist on your network, providing hints attackers may use to find a vulnerability to exploit.
Egress filtering can even help you identify successful exploits before they turn into full-scale attacks. A properly tuned egress filter could detect and block malicious data traveling from an infected network device toward a remote command & control server.
This kind of second-order defense is characteristic of a well-designed information security infrastructure. Even if attackers can make their way past the first obstacle, they find yet another one in the way.
Lumifi uses technologies like egress filtering to build security layers that complement one another. Our analysts have seen these technologies help prevent cyberattacks in the real world, and we use the insights from those experiences to build better, more secure policies as a result.
For instance, we have a client who discovered that a system on their network had begun receiving suspicious DNS requests. Our investigation determined that those requests were malicious command & control instructions coming from a foreign country.
Our solution involved enabling egress filtering for DNS requests. This meant that only the network' domain controller would be allowed to make DNS requests outside the network. Every other system would make requests from the domain controller, who would then process those requests on their behalf.
This measure effectively cut off communication between the malware and its command & control infrastructure. Even if multiple instances of malware exist throughout the network, they would all have to connect to the same domain controller. Their attempt would be blocked, and the firewall would log the suspicious request and send it to the SIEM.
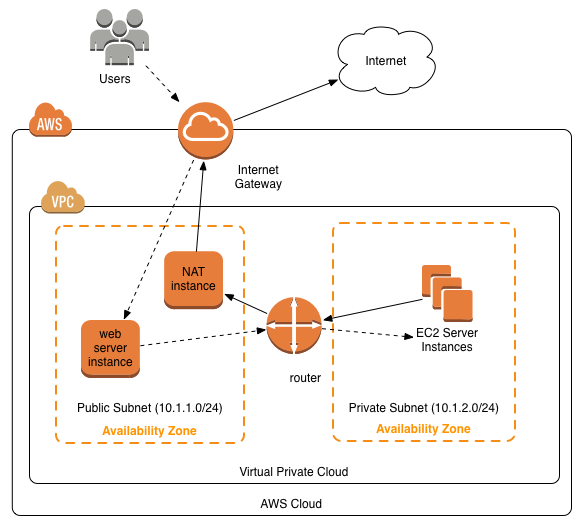
This is a simple and effective way to mitigate cyberattack risks without heavy resource usage or usability impact. In this scenario, the network has a clearly defined perimeter, but the concept applies just as well to complex cloud environments. In fact, it' a critical part of cloud security infrastructure.
Cloud-enabled enterprise IT teams use containerization solutions like Docker to spin up entire IT environments on-demand. This enables an incredible boost in productivity since it vastly reduces the need to maintain complicated legacy infrastructure for different business needs. However, these rapidly changing cloud environments aren't adequately protected unless they have stringent outflow controls.
Virtual private cloud deployments may have their own lines of communication with the outside world, and these may change dramatically depending on the configuration of the deployment. Cybercriminals with zero-day capabilities can (and do) scan for unsecured container deployments, using those deployments' data outflows to identify and ultimately exploit them.
Properly configured, egress filtering helps control the data flowing out from cloud environments. It denies cybercriminals the information they need to identify and exploit vulnerabilities in those environments.
Configuring egress filters to appropriately handle containerized environments on cloud infrastructure is a demanding technical task. Maximize the efficiency of your enterprise security team by delegating responsibility to highly capable security experts. Lumifi provides 24x7 managed detection and response services alongside enterprise-ready SIEM deployment consultation ideal for improving your organization's cloud security profile.
Subscribe to Lumifi's Daily Cybersecurity News Curated by a CISO
Date: 01.28 | Time: 1:00 PM MT