- Solutions
- ShieldVision™
- By Use Case
- Industries
- SOC
- Visibility Triad
- Knowledge Center
- Partners
- Company
- Talk to an Expert
We can help with that.
What we need to establish first is how does your organization handle the compliance regarding your company' and customer' data? Where does that data reside? Is it secure, and if you needed to recall aging data from your system, could you do so with ease?
These are all essential data security questions that all information security team leaders should be asking.
Typically compliance is an unavoidable part of the following industries:
If your business falls into these categories, you are already well aware of compliance' effects on your day-to-day decision-making. There are particular guidelines that your business has to operate under, and your business experiences regular audits to ensure that these procedures are being carried out.
These same compliance methodologies have to be applied to your business' security posture, so selecting a SIEM (or Security Information and Event Management) platform that can meet all your compliance needs is critical.
Excellent question; let's use the analogy of a library.
You access it daily, analyzing logs and users that need immediate attention. Your cloud archive is the stacks. They are there for your historical research and investigation when the active pool in the data lake has aged out.
Logs that begin to age and are not needed for immediate use get sorted back to the cloud archive if you need them - or in the case of compliance - you experience an audit.
Where should you start when searching for a SIEM that meets your compliance needs?
The first question your organization needs to answer is, "what categories does your compliance fall into?"
For example, if you are a medical application that accepts online payments, your company will need HIPPA compliance and PCI (Payment Card Industry Data Security Standards). In addition, your organization could also fall into California' Consumer Privacy Act, and if your reach is international, GDPR (General Data Protection Regulation) could be applicable in Europe.
Each act, regulation, and standards have their specific requirements; however, at the end of the day, the most important feature a CISO and their analysts' needs is the ability to secure data and continue to compile it in an orderly manner over time.
The goal of Data Lake is to present log data to the user in a clear and consumable manner. Log data isn't necessarily designed to be easily read by humans, and finding what really matters can be time-consuming. - Exabeam
A data lake is where all of your organization' data lives to be accessed, analyzed, and utilized by your internal team. This is also where Exabeam' UEBA technology goes to work, analyzing the interactions and behaviors of users, which is an integral part of your SIEM' function.
As the quote from Exabeam above states, data isn't always organized in a user-friendly manner, and for compliance purposes, that could be a significant issue.
Exabeam wants to take the stress out of the data log and retrieval process with an easy-to-use user interface and several pre-made reports that are available to users so that you can pull the exact data you need with minimal effort.
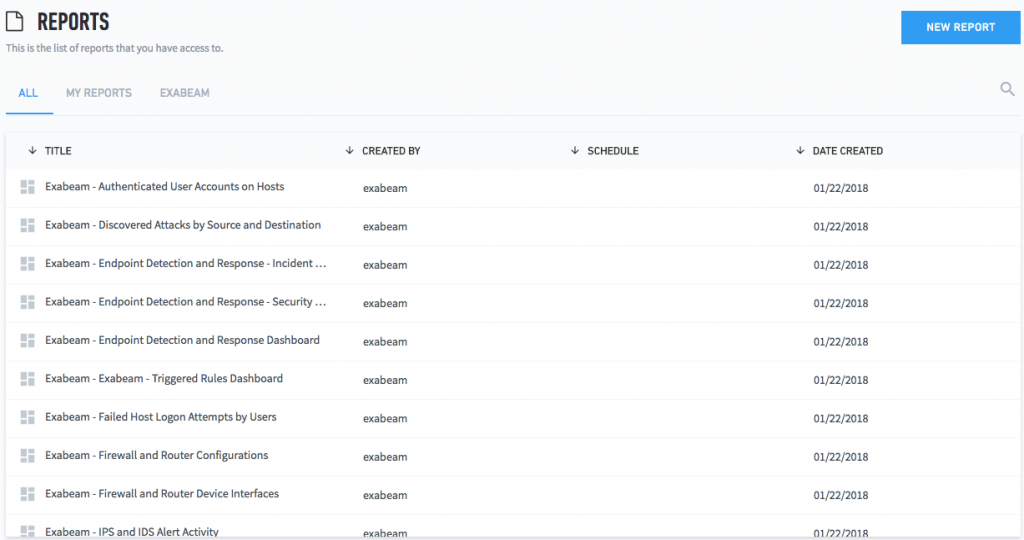
SOURCE: EXABEAM
Many organizations either operate without or solely with a data lake, but depending on how urgent your need is for easy access to data even a year later, or your compliance guidelines require you to keep your data for an extended period of time, the cloud archive may be a solution that your organization should add in addition to the data lake.
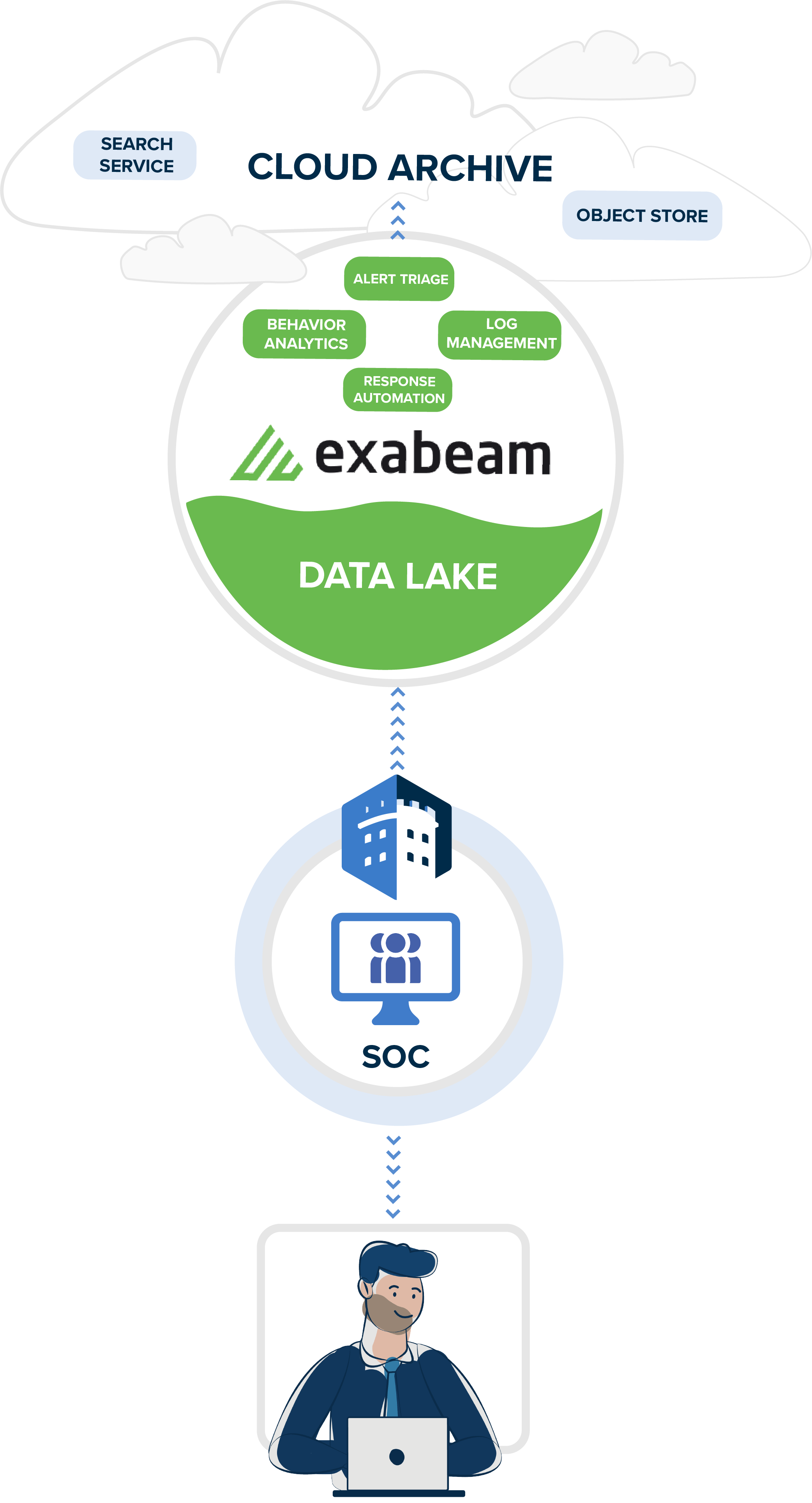
Your SIEM' Cloud Archive is the ever-growing storage of your data lake.
Here data that may not be an immediate need, but could be that "someday, maybe" need for investigations resides. Exabeam takes this archive and levels up its user experience. Much like their Data Lake option, Exabeam' Cloud Archive makes it easy for analysts to search through all of their logs.
One of our information security experts can talk through your current needs, help explain your options, and find the best solution for your data needs.
We’ve expanded our MDR capabilities with enhanced incident response and security services to better protect against evolving cyber threats.